API attacks have skyrocketed by 3000% in 2024, far outpacing traditional web threats. Because APIs now handle the majority of digital interactions, attackers are finding new ways to exploit their trust model.
DDoS tactics have moved up the stack. Rather than just flooding networks, attackers increasingly target APIs by sending legitimate-looking requests that strain application resources and cause slowdowns or outages.
For example, a malicious actor could use the PUT method to edit or delete a customer’s data via valid HTTP requests. The system sees it as normal activity until financial losses and reputational damage are already done.
In other words, attackers are getting better at evasion. These legitimate-looking requests can exhaust an API’s core functions or disrupt workflows – issues known as business logic flaws.
API Security in the Agentic AI Era
APIs are among the most critical vulnerabilities in modern digital infrastructure because they are the pipelines that passthrough firewalls and connect directly to systems. In 2024, API calls constitute over 70% of all web traffic, and the average enterprise manages over 600 API endpoints. Yet, most organisations lack continuous real-time API monitoring.
Now, at the dawn of the Agentic AI era, these risks begin to multiply. Every AI agent connects through APIs by extracting data from servers, issuing commands, linking to third-party apps, or coordinating with other AI agents to directly access the API control plane. Without visibility in behavioural context, organisations are flying blind while AI agents operate with full system access.
Traditional tools were never built to handle this challenge. They inspect traffic at the edge and filter payloads but they can’t detect rogue AI agents exploiting shadow APIs.
At Conversant Solutions, we recognise that APIs are more than code interface. APIs carry business logic, data and authentication flows that attackers systematically exploit through methods traditional security cannot detect. MaxiSafe Web Application and API Protection (WAAP) secures these blind spots with comprehensive, behaviour-aware protection.
Five Critical Blind Spots MaxiSafe Addresses
These risks aren’t new, the rise of Agentic AI changes their scale and speed. Automated systems now issue API calls, process data, and trigger workflows without human input.
The gaps below explain where API security falls short, and how MaxiSafe addresses them.
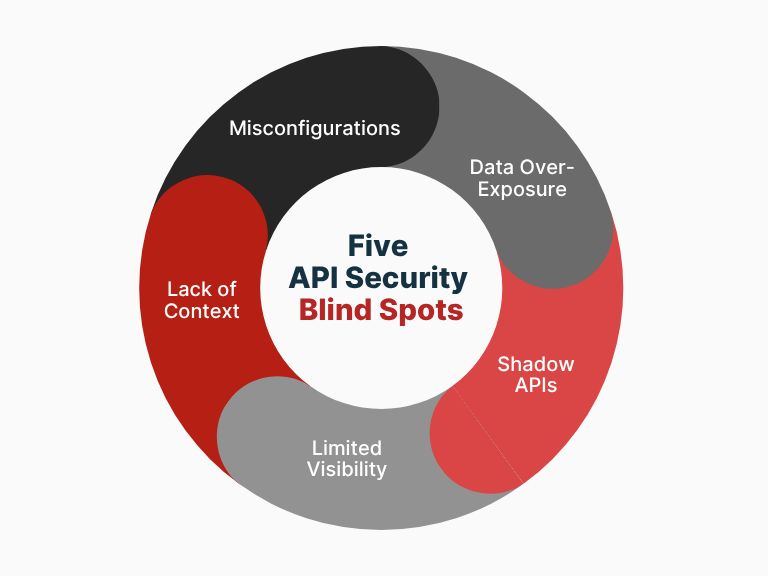
1. Shadow APIs – Undocumented, Unknown APIs
The most dangerous APIs are the ones you don’t know exist. Development teams often deploy test APIs, temporary integrations, or launch new features with API connections that never make it to documentation. These “shadow APIs” become exploitable entry points.
MaxiSafe’s continuous API discovery automatically maps entire API ecosystems in, identifying every endpoint, parameter, and data flow. Its schema validation detects unusual requests and parameter combinations, and triggers alerts on attempts to access undocumented APIs for immediate review.
2. Overexposure of Sensitive Data
APIs often handle confidential information from user IDs and phone numbers to payment details and access tokens, yet many responses expose more data than necessary.
Unprotected payloads or misconfigured responses can unintentionally leak these sensitive data, leading to compliance and reputational risks.
MaxiSafe adopts a proactive security approach when sensitive data is involved. It does so by actively scanning API payloads and automatically masking confidential fields before they leave your environment. This approach effectively prevents inadvertent exposure in API responses.
3. Misconfigurations and Weak Authentication
APIs can fail silently when parameters, data handling, or authentication are misconfigured. A single permissive query or misplaced credential can expose data or system commands to attackers through everyday operational settings.
Detecting these issues early requires visibility into how APIs behave in production. MaxiSafe’s API Vulnerability Detection capabilities provide that visibility by analysing API activity in real-time and matching requests and responses against managed detection rules.
It helps detect patterns such as:
- Access permission risks
Parameters that execute commands, run database queries, or expose full file paths. - Data exposure
Personal or confidential information appearing unmasked in API responses. - Weak authentication
Passwords or tokens sent insecurely through cookies, URLs, or plaintext responses.
Vulnerabilities discovered are categorised by type and severity to help teams fix them quickly, confidently, and strengthen overall API resilience.
4. Existing Defences Don’t Understand API Behaviour
Legacy defences often treat each API activity as a standalone event – counting requests, flagging payloads, and blocking based on simple rules or thresholds. This makes them ineffective against Business Logic Attacks (BLAs), which exploit intended application workflows in unintended ways or through abnormal usage patterns.
For example, during a product launch or flash sale, APIs are hit with large bursts of valid-looking calls. Attackers exploit this by replaying genuine workflows or targeting logic intended for “normal” use. Each request appears legitimate but in context, they form a pattern of abuse that can distort business metrics, slow critical processes, or lead to data and revenue loss.
Static security rules see the individual calls and rate-based thresholds, but miss the bigger picture: the workflow state, user intent, and request sequencing. Without this context, defences either throttle legitimate users or allow malicious bots to disguise as part of real traffic.
MaxiSafe’s Programmable Mitigation fills the gap by learning and adapting to how your workflows behave, not just how they look. It applies policies based on the context of activities – escalating when patterns diverge from normal logic, and relaxing when they align.
- Adds unpredictability (in app responses and timings) to prevent attackers from mapping system behaviour.
- Apply stricter verification for suspicious activity while keeping trusted sessions uninterrupted.
- Configure protection policies on workflow to secure multi-step API transactions.
This behavioural context-aware approach helps protect sensitive API workflows, even as user activity and workloads evolve in real time.
5. Limited Real-Time Visibility
The longer an API attack goes undetected, the greater the damage. Hours of undetected data exfiltration can cost millions, yet 80% of organisations lack continuous, real-time API monitoring. And as AI agents increasingly automate API calls and data exchanges, real-time visibility becomes essential to detect abnormal or autonomous behaviour before it escalates.
MaxiSafe helps overcome this visibility gap by continuously monitoring live API behaviour to detect suspicious activity, and connects all you need into its SwiftFederation dashboard.
When anomalies emerge, MaxiSafe immediately translates them into actionable security alerts. This turns API visibility into active defence that helps teams act fast to eliminate threats.
MaxiSafe closes this visibility gap with continuous monitoring that analyses live API behaviour for suspicious activity. When anomalies emerge, MaxiSafe translates them into actionable alerts, helping teams detect and respond faster to threats.
This visibility is consolidated into the SwiftFederation dashboard, providing a single view on security metrics for web application and API protection insights. With real-time insight and context, security teams can turn visibility into active defence and stop attacks before they escalate.
From Blind Spots to Full Control
With over 70% of all web traffic now API-driven and most organisations lacking real-time monitoring, blind spots in API ecosystems present serious business risks.
And as agentic AI systems begin to interact directly through APIs, the risk landscape becomes even more dynamic.

That’s why protection can no longer be fragmented. Security must be proactive and work as one.
With MaxiSafe’s unified Web Application and API Protection (WAAP), businesses gain the visibility, context, and control needed to close critical blind spots. It simplifies operations and accelerates response to help teams stay ahead even as threats evolve across an increasingly AI-driven world. Learn How MaxiSafe Works >>
Secure your web apps today. Start Free Trial >>



