
Web Application and API Protection (WAAP) is a security solution designed to protect web applications and APIs from wide range of cyber threats. As organisations increasingly rely on these applications and APIs for business-critical operations, the attack surface expands, exposing them to misuse, automated abuse, and attacks that target application logic.
WAAP addresses this risk by continuously monitoring application traffic, analysing behaviour, and enforcing security controls to prevent malicious activity. In practice, it is commonly adopted to protect critical interfaces such as customer-facing websites, mobile application backends, and APIs that connect internal systems or third-party services.
Why is WAAP Important?
As web applications and APIs evolve, so do the threats against them. Attacks have moved beyond basic exploits to include automated abuse, business logic manipulation, and subtle API-level attacks that are difficult to detect using traditional security controls. Many of these attacks do not rely on known vulnerabilities, making them harder to identify and mitigate using rule- or signature-based approaches alone.
Limitation of Web Application Firewalls (WAFs)
Traditional WAFs have long been used to protect web applications, but their design reflects an earlier threat landscape. They rely primarily on static rules and signature-based detection, which makes them effective against known attack patterns but inherently reactive. As a result, emerging attack techniques, unusual traffic patterns, and abuse that targets application logic may go undetected.
Maintaining effective protection often requires frequent rule updates and ongoing tuning. This can be resource-intensive and introduces operational risk, as gaps between updates or misconfigurations can leave applications exposed.
Over time, rule-based approaches also struggle to scale with increasing traffic volumes and evolving attack methods. As applications and APIs grow more complex, these limitations can create blind spots that traditional WAFs are not designed to address.
While traditional WAFs have limitations when deployed on their own, their core capabilities remain an important part of modern application security. WAAP builds on these foundations by integrating WAF functionality with additional, application- and behaviour-based protections.
How does WAAP Security Work?
WAAP security is designed to protect modern web applications and APIs by combining multiple protection capabilities into a unified, application-aware security layer. Rather than relying solely on static rules, WAAP continuously monitors traffic patterns, analyses behaviour, and enforces controls across web, API, and automated traffic in real time.
By correlating signals across different types of traffic, WAAP is able to detect and mitigate threats that target application logic, abuse exposed APIs, or attempt to overwhelm services through automated or volumetric attacks.
Core WAAP Protection Capabilities
WAF
Protects against application-layer attacks and common web exploits by analysing HTTP requests. Predefined rules and signatures are used to inspect parameters, cookies, and session data to detect threats such as OWASP Top 10 risks, SQL injection, and cross-site scripting.
API Protection
Protects applications from automated abuse such as credential stuffing and content scraping. Traffic patterns, request frequency, and interaction behaviour are analysed to distinguish legitimate users from malicious automation, while allowing trusted partners and third-party bots to operate without disruption.
Bot Management
Protects applications from automated abuse such as credential stuffing and content scraping. Traffic patterns, request frequency, and interaction behaviour are analysed to distinguish legitimate users from malicious automation, while allowing trusted partner and third-party bots to operate without disruption.
DDoS Mitigation
Protect against large-scale, protocol-based attacks on the application layer by continuously monitoring request rates and traffic behaviour. When abnormal activity such as sudden spikes is detected, controls such as rate limiting and filtering are applied to maintain service availability.
How MaxiSafe Secures and Optimises Web Applications and APIs?
While WAAP provides a framework for protecting modern applications and APIs, MaxiSafe is Conversant’s implementation of this approach. It combines application and API security with integrated traffic management and centralised visibility, helping organisations protect and operate their digital services more effectively.
By unifying security controls and content delivery within a single platform, MaxiSafe enables real-time threat mitigation while maintaining application performance and availability, even under changing traffic conditions.
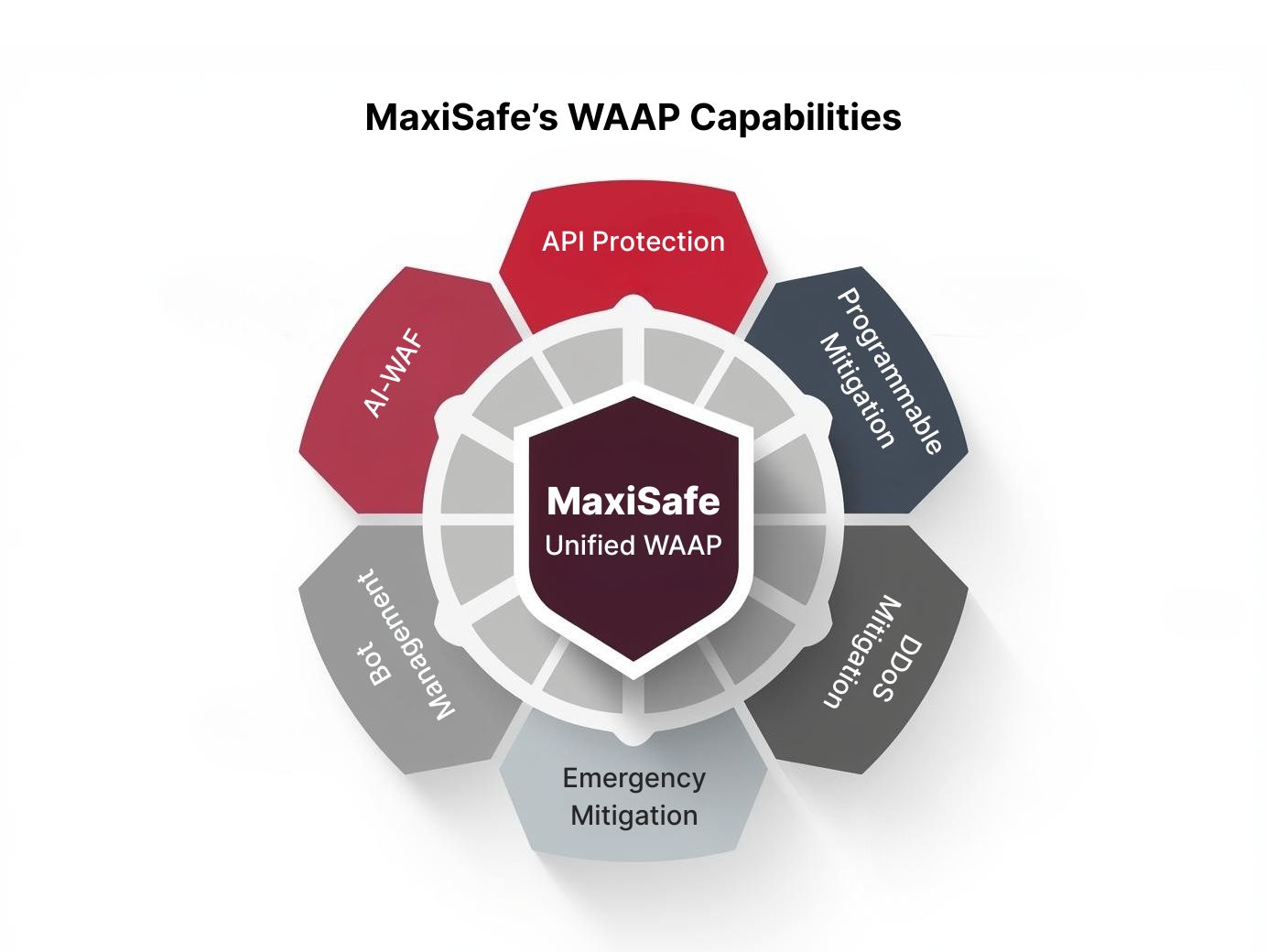
Core MaxiSafe Capabilities
AI-powered WAF
Extends traditional WAF protection by analysing request patterns and user behaviour in real time. Self-learning models adapt to injection attacks, cross-site scripting, and evolving OWASP Top 10 threats, helping reduce false positives and the need for continuous manual rule tuning.
API Protection
Extends traditional WAF protection by analysing request patterns and user behaviour in real time. Self-learning models adapt to injection attacks, cross-site scripting, and evolving OWASP Top 10 threats, helping reduce false positives and the need for continuous manual rule tuning.
Bot Management
Distinguishes legitimate users from malicious automation through real-time risk assessment. Adaptive challenges and behavioural analysis allow trusted bots to operate normally while blocking automated abuse such as credential stuffing and content scraping.
DDoS Mitigation
Maintain availability during application-layer flood attacks. Traffic is absorbed and filtered at the edge to prevent backend resource exhaustion, with automated rate limiting applied when abnormal request patterns are detected.
Content Acceleration
Improves application performance and availability through an integrated CDN. Dynamic and static content caching at the federated edge reduces latency during normal operation and traffic spikes, while global load balancing routes users to the most optimal point of presence with built-in failover.
Advanced Security Controls
Programmable Mitigation
Enables tailored responses to abnormal or abusive traffic based on application behaviour. Controls such as rate limits, geo-based restrictions, and surge handling can be applied dynamically to protect critical workflows.
Business Threat Awareness
Surfaces suspicious activity that may not trigger traditional alerts, including abnormal sign-ups, promotion abuse, or transaction anomalies. Insights are derived from behavioural analysis combined with internal and external threat intelligence.
Emergency Mitigation
Allows rapid containment of active threats through emergency controls such as traffic restriction modes, static-mode and kill switch, helping teams stabilise systems while incidents are investigated.
Turn Complexity into Confidence
MaxiSafe is designed to simplify the protection and operation of modern web applications and APIs. By unifying application security, API protection, traffic management, and centralised visibility within a single platform, it helps teams manage complexity without sacrificing performance or control.
This integrated approach reduces operational overhead, improves response to emerging threats, and provides clearer insight into application behaviour. As a result, teams can focus less on reactive firefighting and more on maintaining reliable, secure digital services.
>> Learn more about how MaxiSafe works.
>> Trial MaxiSafe for free.
Get started with a free trial to explore how MaxiSafe protects and optimises web applications. No lock-in period, cancel anytime.



