Automate WAAP to block bots, API abuse and DDoS with less rule-tuning. Learn how WAAP automation frees up your team.
Solution Brief
WAAP Automation: Save Time and Reduce Manual Work

Your web applications and APIs are the digital front doors to your business. Whether you’re running an e-commerce platform, a streaming service, or a B2B portal, you’re relying on API-driven experiences to deliver fast, seamless service. An API-driven approach designs and builds the APIs first, then the rest of the application around them, making it easier for external systems to access features without dealing with database complexities.
But with that reach comes inherent risks. APIs introduce complexity, and that complexity creates vulnerabilities. (Learn the common API gaps)
The Rising Tide of Web Apps and API Threats
In 2024, API cyber attacks in Asia-Pacific rose 65% year-on-year, and 271 million API attacks were recorded in a single quarter. Each API faced 3,000% more DDoS attacks than a typical website and 85% more attacks than traditional web applications.
The trend is mirrored in Southeast Asia
- Vietnam: 46% of businesses targeted in H1 2024, with incidents exceeded 659,000 in full year.
- Indonesia: Over 315,000 credentials compromised in H1 2024, more than 60 every hour.
Without proper testing, authentication, and validation, businesses leave themselves exposed, and teams often end up in a constant firefight, bogged down in manual work.
How Manual Security Tasks Hold You Back
Cyber threats don’t merely impact websites, they disrupt business. Traditional approaches weigh down your team with updates, manual rule changes, bot-blocking, and endless log reviews. These repetitive tasks take time away from growth.
Common time-consuming tasks include:
- Updating firewall and access policies
- Blocking bots and suspicious traffic patterns
- Monitoring for API abuse and unauthorised access
- Investigating DDoS attacks or slowdowns during peak usage
- Managing false positives that impact user experience
Without automation, these tasks require constant tuning and round-the-clock vigilance that keep your personnel consumed with labour-intensive tasks.
The challenge is magnified by the rise of AI-powered cyberattacks. In 2024, a staggering 87% of organisations experienced such attacks, yet only 26% felt confident in their ability to detect them. Cybercriminals use AI to automate and enhance their methods, making attacks more sophisticated, targeted, and harder to detect manually. This keeps security teams stuck in a reactive loop – always chasing the next threat instead of staying ahead.
WAAP: Security That Works for You
With Web Application and API Protection (WAAP), you get a smarter way to protect digital assets. Delivered at the edge, it identifies and blocks threats before they reach your app or API. A typical WAAP solution takes the burden off your team: fewer emergencies, faster launches of new digital services, and more time for staff to focus on strategic priorities instead of firefighting. The automation built into WAAP reduces manual intervention, improves detection, and keeps you protected even when your team is off the clock.
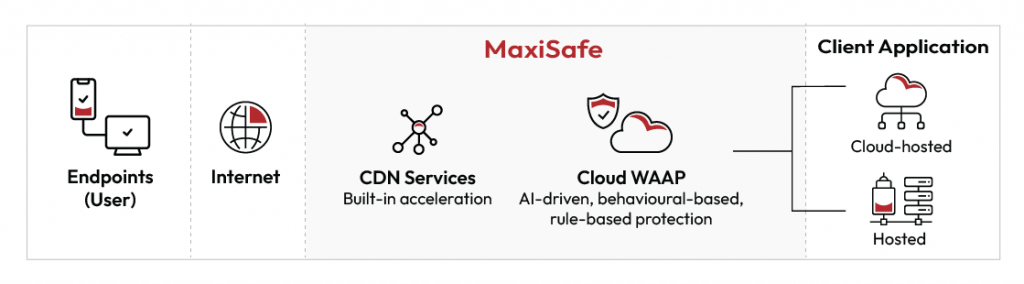
WAAP Automation Saves Time and Strengthen Web App Security
With WAAP, you integrate multiple defences – WAF, API protection, bot mitigation, and DDoS shielding, into a single solution. When infused with AI, machine learning, and behaviour-based analysis, WAAP offers several automated protections:
- AI-powered Web Application Firewall (AI-WAF)
Adaptive rules to block known and unknown threats - Intelligent bot management
Detects and differentiates between good and malicious bots in real time - API protection
Studies traffic and user behaviour to enforce security with minimal inputs - DDoS mitigation
Automatically triggers behavioural-based blocking - Dashboards & alerts
Actionable insights without manual log-mining
Turn Security Burdens into Advantages
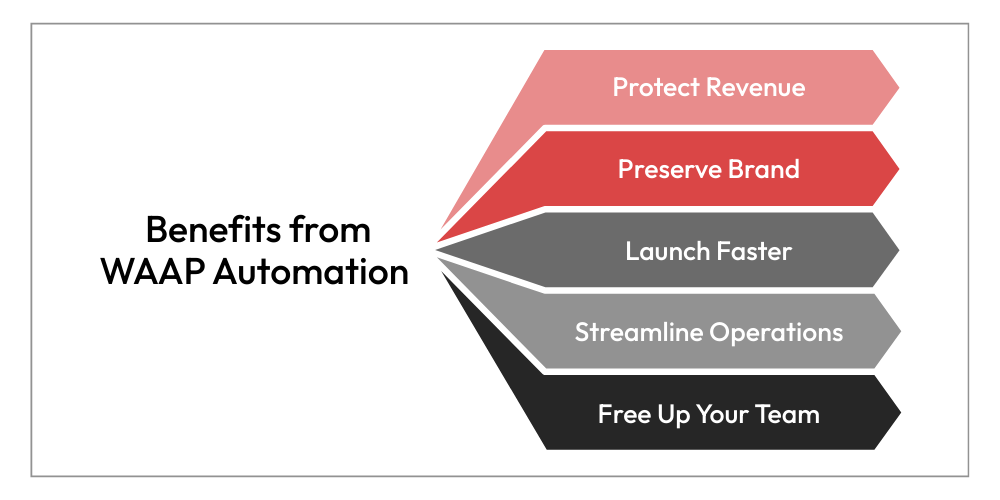
With WAAP, you can turn security from a constant operational burden into a background strength, so your web teams can move faster, build more, and spend less time reacting. It improves your IT team’s efficiency without increasing headcount.
Key time-saving benefits include:
- Protect Your Revenue
Avoid the cost of downtime and breaches, and automatically block threats before they cause damage. Integrating WAAP tools with your existing security defences can limit the percentage of false positives and negatives. - Preserve Your Brand
By staying ahead of breaches, you preserve trust, and potentially save millions in lost revenue and brand repair. - Streamline Your Operations
Cut manual security tasks and reduce workload with less patching, fewer hot fixes and manual rule-setting. Some businesses see a 20–40% drop in operational security costs with WAAP.[1] - Launch Faster
Secure new applications and APIs right away and get to market 30–50% faster.[2] - Free Up Your Team
With 33% faster incident response and 43% better prevention when AI and automation are deployed, your team spends less time fighting fires and more time building great experiences.[3]
Reduce Manual Work, Reduce Downtime with MaxiSafe WAAP
MaxiSafe offers multi-layered, AI-driven protection for today’s evolving threat landscape. Designed to ensure your business stays online, responsive and secure, it combines intelligent detection, risk reduction and management, and business-threat awareness in a single solution.
MaxiSafe gives you:
- Accurate threat detection with fewer false alarms
- Real-time bot filtering
- Built-in API data protection and masking
- DDoS attack defence powered by behaviour analysis
- Continuously updated protection aligned to OWASP standards and PCI-DSS requirements
- Simple dashboard and management tools
- Built-in CDN for performance optimisation
Together, these capabilities give you a security solution that’s easier to manage and faster to act. You can explore the list of features, and take advantage of MaxiSafe free trial.
Explore MaxiSafe: MaxiSafe overview · Brochure · Pricing & FAQs
Sources:
1. Forrester Total Economic Impact™ of Cloud WAAP Solutions, 2022
2. Gartner Research: API Security and Application Development, 2022
3. Cost of Data Breach Report 2024



